Regardless of our profession, we all need clear policies. If you were a kindergarten teacher, would you have rules for your students?
Of course you would – or else you would be running around with play-do in your hair, food all over the walls, and oh my word Jimmy – that bookshelf is not a ladder!
While your key system isn’t quite as rambunctious as a 4-year old, it can make you want to pull your hair out all the same. Hence the need for key system policies that everyone clearly understands, but where do you begin on implementing them?
Key System Policies
1: How many keys should be issued per store?
It’s never good to have too many keys floating around – over-abundance makes it easy to lose track of them and damage the integrity of your system. On the flip side, too few keys can slow down store operations.
 Earlier in this series we discussed what purpose you want your system to serve and your answer plays a big part in how many keys you want in place. If you want your key system to provide a tight level of security, you should limit the number of keys issued. Do you use the alarm as the main security feature? If so, you may be more inclined to issue a larger number of keys.
Earlier in this series we discussed what purpose you want your system to serve and your answer plays a big part in how many keys you want in place. If you want your key system to provide a tight level of security, you should limit the number of keys issued. Do you use the alarm as the main security feature? If so, you may be more inclined to issue a larger number of keys.
2: Who Carries the Keys?
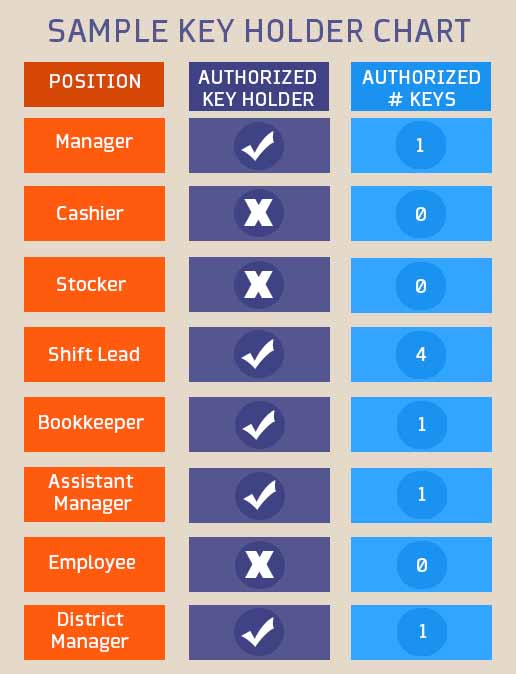
It sounds simple, but is often overlooked. Be certain that everyone involved is aware of what positions within the company are authorized to carry keys. This makes key orders, rekeys, and system integrity easier to manage.
If you are on a master system, this step is crucial. Make sure everyone in your organization that utilizes the key system – from top level corporate management down to the store level – understands not only who is authorized to carry keys, but who is authorized to carry each level of key. You definitely don’t want your cashier to be carrying around the grand master key – no bueno.
3: How are key orders placed?
Again, this is a simple concept, but an important one. Unauthorized employees ordering keys is a recipe for trouble. Make sure that you and your key system vendor have a clear understanding of who is authorized to order keys, and hammer out an order process that your entire organization understands. Generally, once you have the process in place you will be responsible for informing your team internally, and your vendor will carry out the compliance aspect. If someone who isn’t authorized to order a key calls your vendor (or a step in the process has been skipped), your vendor will instruct the requesting person on the proper steps to follow. We’ll talk more about this next week.
4: When is the key system installed on new store openings?
Do you want the plumber, drywall contractor, or painter to have a key to your store? Probably a bad idea, right? Yet, we have seen it time and again where a key system is installed early in the construction process. Doing so risks the integrity of your system, especially if it is unrestricted.
We recommend using construction cores during construction, and then just before the store is turned over, install the key system. This will help maintain the integrity of the system – you (not the GC) have control over who has the keys to each store.
5: What is your rekey protocol?
This is a crucial policy with a lot of considerations. Rather than dive into it today, we will address in a two weeks.
It’s important to note that having key system policies only takes you so far. I cannot stress enough the importance of ensuring that both your key system vendor as well as everyone in your organization from the top to the bottom understands and abides by these policies. Failure to do so can make you look like the kindergarten teacher with play-do and God knows what else in your hair; you’ll be left cleaning up the mess of a key system that has lost its integrity.
Now that you have your key system policies laid out, it’s time to define the procedures that enforce them – more on that next week. Until then, let us know what questions you have in the comments section below!
Check out our Key Systems 101 article for more information.
[maxbutton id=”1″]
Check out the rest of our series:
The Five Critical Components of Key System Management
Key System Types: Restricted, Unrestricted, and Proprietary
Proprietary & Restricted Key Systems
Standard Cylinders versus Interchangeable Cylinders – What’s the Difference?
eCylinders – The Amazing, The Mundane, and The Considerations
Rekeyable Cylinders – Fast, Easy, & Cost Effective
Master Key Systems – Controlled Access With One Key
Key System Policies – Keep Your System In Tact
Key System Procedures – A Roadmap for Maintaining Your System’s Integrity
Rekey Policies & Procedures – Three Elements to Consider
Key System Records Management – 4 Cornerstones

There is certainly a lot to learn about this subject. I really like all of the points you have made.