Key systems can be a daunting task to manage; whether you’re starting from scratch or re-vamping your current system we’ll help you delve into every aspect of key system management. From choosing a system to establishing your policies and procedures we’ll walk you through the difficult tasks as well as the ones you probably haven’t thought about.
To kick this series off right, we’ll start with the basic principles of key system management. Over the next few weeks, we’ll analyze each component outlined here. If we miss something you’re anxiously waiting to learn more about drop it in the comment section below; we’ll circle back as many times as necessary.
The Five Critical Components of Key System Management
Many organizations have key systems in place, but unless they are setup and managed properly, they can become ineffective and/or cost the organization hundreds to thousands of dollars in unnecessary rekeys. The truth is that there is a gradient of key control, and organizations land somewhere on the scale. Your job is to decide if you are comfortable with where your organization is on that scale. I want you to ask yourself a few questions:
- Do you know of every locked door/cabinet in your domain? Are they documented?
- Who holds the keys to all of those doors?
- Is your system on restricted keys?
- If a key was reported as lost, would you rekey?
- If you had an event, who has the keys to that door?
- Is there a single individual at your organization responsible for the management of all of this?
- Is all the relevant data computerized and backed up?
How did you do? How do you feel about the gaps in your key system you just identified? Is there a level of risk with any of these gaps? If so, are you comfortable with them? If not, you’re in the right place to start the re-evaluation of your program. There are  many components to consider but the five that prove to be the most critical are:
many components to consider but the five that prove to be the most critical are:
- Key System Philosophy
- Records Management
- Rekey Avenue
- Procedures
- Policies
1. What key system philosophy do you want to follow?
The first step is the most basic – what purpose do you want your key system to serve?
- Should keys simply lock the doors, or do you want them to be restricted and/or serve as an audit trail?
- Do you want a system that can easily be rekeyed that costs more up-front, or do you want a standard system that is more costly to rekey?
- Does your facility require personnel to have access to different doors with the use of a master key system?
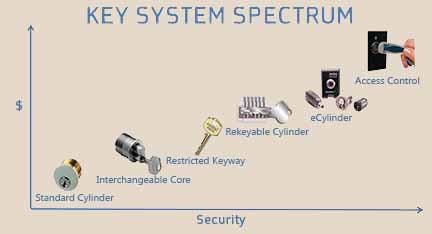
Answering these questions will help you determine a starting point for the many different types of key systems out there. The varieties include: un-restricted, restricted, proprietary, and access control. In addition to the variety of systems, there are also a large variety of cylinders available including: standard cylinders, interchangeable cylinders, rekeyable cylinders, and eCylinders. We will detail each type of system and cylinder later in this series.
2. What policies do you and your key system vendor need to have in place?
Once you select a system, it is crucial that you outline your policies and implement a structure that will enforce them. Without enforced policies, the best planned key system will fall apart. Critical policies to develop include but are not limited to:
- How many keys should be issued per store?
- Who is allowed to carry those keys?
- If you have a master system, which personnel are allowed to have access to which doors?
3. What procedures do you and your key system vendor need to have in place?
Procedures for your staff, upper management, and key system vendor should be clear and concise so that everyone in your organization understands and enforces. Some policies to consider include:
- How does one ask for and receive a key?
- How are lost/stolen keys reported?
- How are keys distributed to contractors?
- When are cores installed during the construction process?
4. What is your rekey protocol?
Regardless of the type of key system you choose, rekeys will be necessary. In addition to establishing a protocol for when re-keys are necessary, you should also establish your re-key avenue with your key system vendor. This process should be available to anyone who will be regularly authorizing re-keys.
We have seen rekey requests for reasons ranging from “I flushed my key down the toilet” to “someone stole my keys in the store.” The latter certainly necessitates an emergency rekey, while the former poses very little, if any, threat to the security of the facility. A clear policy and procedure that dictates when and how rekeys are to happen should exist.
5. How will your key records be managed?
Records management is essential to the success of any key system. Your records should be computerized, as automated as possible, well maintained, backed up, and owned by your organization. Paper records are highly susceptible to human error and can easily get lost; believe it or not, there are still a lot of paper records out there.
Most importantly, you should be the owner of your key system, as opposed to the vendor managing the system. That way, should you ever decide to part ways, you don’t risk losing your system or records.
That’s it! You’re well on your way to implementing a key system that is well maintained and cost effective. We’ll take the next steps next Tuesday. Don’t forget to leave your questions in the comments section below!
A version of this article first appeared in the May issue of Service Channel’s Contractor Corner – see it here.
Check out our Key Systems 101 article for more information.
[maxbutton id=”1″]
Check out the rest of our series:
The Five Critical Components of Key System Management
Key System Types: Restricted, Unrestricted, and Proprietary
Proprietary & Restricted Key Systems
Standard Cylinders versus Interchangeable Cylinders – What’s the Difference?
eCylinders – The Amazing, The Mundane, and The Considerations
Rekeyable Cylinders – Fast, Easy, & Cost Effective
Master Key Systems – Controlled Access With One Key
Key System Policies – Keep Your System In Tact
Key System Procedures – A Roadmap for Maintaining Your System’s Integrity
Rekey Policies & Procedures – Three Elements to Consider
Key System Records Management – 4 Cornerstones
Google

Very informative article post.Really looking forward to read more. Really Great.
We are looking for 5 sets of door locks with master keys
Hi, Richard! Please give our office a call at 859-887-9119 and we’ll be able to help you.